Data Diode Products
What is Owl Data Diode
Data Diode Purpose
Yes, data diodes can be implemented in a specialized configuration to facilitate two-way data transfers, while still providing hardware-enforced network segmentation. Owl’s ReCon is a highly tailored, proven hardware-based cybersecurity solution utilizing two independent one-way paths in a single unit, with each path protected by a data diode. However, the transfer can only be initiated from the “high” security side of the network connection. This approach enables network segmentation, remote command and control, remote monitoring, and SCADA data replication, with significantly less risk than a standard software firewall.
Can data diodes be used for two-way data flows?
Yes, data diodes can be implemented in a specialized configuration to facilitate two-way data transfers, while still providing hardware-enforced network segmentation. Owl’s ReCon is a highly tailored, proven hardware-based cybersecurity solution utilizing two independent one-way paths in a single unit, with each path protected by a data diode. However, the transfer can only be initiated from the “high” security side of the network connection. This approach enables network segmentation, remote command and control, remote monitoring, and SCADA data replication, with significantly less risk than a standard software firewall.
Data Diode Products by Form Factor

OPDS - 100
Multi-purpose, Medium Throughput

OPDS - 1000
Multi-purpose, High Throughput

EPDS
Multi-purpose, Very High Throughput

PaciT
Raw Ethernet Packets, Very High Trougput

XD Guardian
Multi-purpose, Bidirectional, Filtering

OPDS - 100D
Multi-purpose, Industrial Form Factor

DiOTa
Single Protocol, Lower Througpu

Recon™
Bidirectional, Secure Command & Control

SSUS

The Owl Perimeter Defense Solution (OPDS) product line is designed to support the Critical Infrastructure markets. These cybersecurity products are oriented around protecting the data networks and digital assets (SCADA, PLCs, DCS, databases, historians, etc.) located at various critical infrastructure facilities including plants, mines, power plants, banks, substations, credit unions, pump stations, oil rigs, etc.
The concept is to protect the control systems within the facility by creating a secure cyber perimeter around the plant so that plant operations are not interrupted, sabotaged or otherwise impacted by some kind of cyberattack. The concern is not only for threats against single facilities (i.e. a nuclear power plants, refineries) but also a coordinated, simultaneous attack that shuts down multiple power substations, freshwater delivery systems or bank branches for example; leading to significant stress, disorder, and in the minds of the attackers, chaos.

Owl Talon™
Data Diode Platform
Secure, Flexible, One-way Transfer
Owl TalonTM is the software layer that operates the device, manages data flows and protocols while allowing the data diode to interact with endpoints on the network. Built on a defense-in-depth strategy, the OPDS hardware and Talon software operate together in a layered approach to defend both the network and hardware from cyber attacks.

Owl Talon MK1000
All-in-one, 19” 1U rack-mountable appliance for secure, high speed one-way data transfers at up to 1 Gbps.

Owl Talon HX600
All-in-one, DIN-Rail mountable appliance for secure, high speed one-way data transfers at up to 1 Gbps.

Owl Talon R660
All-in-one, 2x 1U 19” rack-mountable appliance for secure, high speed one-way data transfers at up to 10 Gbps.
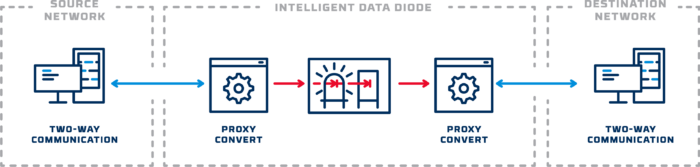
One-Way in a Two-Way World
A successful one-way data transfer requires meeting the expectations of a two-way world. A majority of network traffic involves some sort of acknowledgement or two-way connection in order to function. The “secret sauce” of Owl Talon is in providing a secure one-way transfer, with a true separation between source and destination networks, while maintaining simultaneous, two-way communications with both the source network and the destination network to avoid disruption. This is accomplished through using proxies that run on each side of Owl data diodes.
The send side proxy communicates with the source network acknowledging receipt of packets before extracting the payload and sending it across the diode. On the receive side, the proxy receives the payload, builds a new packet around it using the original protocol and sends the data on its way over the two-way protocol. In this way, the data diode achieves a secure one-way transfer in the middle of two, two-way exchanges.